If you need to expand your server environment beyond a local area network, a Microsoft Remote Desktop CAL is the right solution for you. Remote desktop licenses are add-on s for Microsoft Windows Server that unlock the ability for specific devices or users to access the central server from anywhere they’re located using their existing software. Download Remote Desktop Manager - Remote Desktop Manager (RDM) centralizes all remote connections on a single platform that is securely shared between users and across the entire team.
-->Applies to: Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016
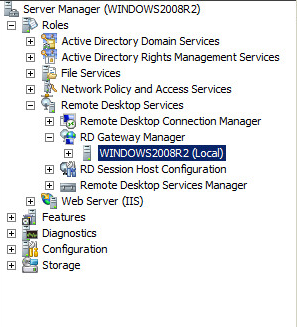
Use the following steps to deploy the Remote Desktop servers in your environment. You can install the server roles on physical machines or virtual machines, depending on whether you are creating an on-premises, cloud-based, or hybrid environment.
Rd Manager Microsoft
If you are using virtual machines for any of the Remote Desktop Services servers, make sure you have prepared those virtual machines.
Remote Desktop Connection Manager Rdg
Add all the servers you're going to use for Remote Desktop Services to Server Manager:
- In Server Manager, click Manage > Add Servers.
- Click Find Now.
- Click each server in the deployment (for example, Contoso-Cb1, Contoso-WebGw1, and Contoso-Sh1) and click OK.
Create a session-based deployment to deploy the Remote Desktop Services components:
- In Server Manager, click Manage > Add Roles and Features.
- Click Remote Desktop Services installation, Standard Deployment, and Session-based desktop deployment.
- Select the appropriate servers for the RD Connection Broker server, RD Web Access server, and RD Session Host server (for example, Contoso-Cb1, Contoso-WebGw1, and Contoso-SH1, respectively).
- Select Restart the destination server automatically if required, and then click Deploy.
- Wait for the deployment to complete successfully
Add RD License Server:
- In Server Manager, click Remote Desktop Services > Overview > +RD Licensing.
- Select the virtual machine where the RD license server will be installed (for example, Contoso-Cb1).
- Click Next, and then click Add.
Activate the RD License Server and add it to the License Servers group:
- In Server Manager, click Tools > Terminal Services > Remote Desktop Licensing Manager.
- In RD Licensing Manager, select the server, and then click Action > Activate Server.
- Accept the default values in the Activate Server Wizard. Continue accepting default values until you reach the Company information page. Then, enter your company information.
- Accept the defaults for the remaining pages until the final page. Clear Start Install Licenses Wizard now, and then click Finish.
- Click Action > Review Configuration > Add to Group > OK. Enter credentials for a user in the AAD DC Administrators group, and register as SCP. This step might not work if you are using Azure AD Domain Services, but you can ignore any warnings or errors.
Add the RD Gateway server and certificate name:
- In Server Manager, click Remote Desktop Services > Overview > + RD Gateway.
- In the Add RD Gateway Servers wizard, select the virtual machine where you want to install the RD Gateway server (for example, Contoso-WebGw1).
- Enter the SSL certificate name for the RD Gateway server using the external fully qualified DNS Name (FQDN) of the RD Gateway server. In Azure, this is the DNS name label and uses the format servicename.location.cloudapp.azure.com. For example, contoso.westus.cloudapp.azure.com.
- Click Next, and then click Add.
Create and install self-signed certificates for the RD Gateway and RD Connection Broker servers.
Note
If you are providing and installing certificates from a trusted certificate authority, perform the procedures from step h to step k for each role. You will need to have the .pfx file available for each of these certificates.
- In Server Manager, click Remote Desktop Services > Overview > Tasks > Edit Deployment Properties.
- Expand Certificates, and then scroll down to the table. Click RD Gateway > Create new certificate.
- Enter the certificate name, using the external FQDN of the RD Gateway server (for example, contoso.westus.cloudapp.azure.com) and then enter the password.
- Select Store this certificate and then browse to the shared folder you created for certificates in a previous step. (For example,Contoso-Cb1Certificates.)
- Enter a file name for the certificate (for example, ContosoRdGwCert), and then click Save.
- Select Allow the certificate to be added to the Trusted Root Certificate Authorities certificate store on the destination computers, and then click OK.
- Click Apply, and then wait for the certificate to be successfully applied to the RD Gateway server.
- Click RD Web Access > Select existing certificate.
- Browse to the certificate created for the RD Gateway server (for example, ContosoRdGwCert), and then click Open.
- Enter the password for the certificate, select Allow the certificate to be added to the Trusted Root Certificate store on the destination computers, and then click OK.
- Click Apply, and then wait for the certificate to be successfully applied to the RD Web Access server.
- Repeat substeps 1-11 for the RD Connection Broker - Enable Single Sign On and RD Connection Broker - Publishing services, using the internal FQDN of the RD Connection Broker server for the new certificate's name (for example, Contoso-Cb1.Contoso.com).
Export self-signed public certificates and copy them to a client computer. If you are using certificates from a trusted certificate authority, you can skip this step.
- Launch certlm.msc.
- Expand Personal, and then click Certificates.
- In the right-hand pane right-click the RD Connection Broker certificate intended for client authentication, for example Contoso-Cb1.Contoso.com.
- Click All Tasks > Export.
- Accept the default options in the Certificate Export Wizard accept defaults until you reach the File to Export page.
- Browse to the shared folder you created for certificates, for example Contoso-Cb1Certificates.
- Enter a File name, for example ContosoCbClientCert, and then click Save.
- Click Next, and then click Finish.
- Repeat substeps 1-8 for the RD Gateway and Web certificate, (for example contoso.westus.cloudapp.azure.com), giving the exported certificate an appropriate file name, for example ContosoWebGwClientCert.
- In File Explorer, navigate to the folder where the certificates are stored, for example Contoso-Cb1Certificates.
- Select the two exported client certificates, then right-click them, and click Copy.
- Paste the certifcates on the local client computer.
Configure the RD Gateway and RD Licensing deployment properties:
- In Server Manager, click Remote Desktop Services > Overview > Tasks > Edit Deployment Properties.
- Expand RD Gateway and clear the Bypass RD Gateway server for local addresses option.
- Expand RD licensing and select Per User
- Click OK.
Create a session collection. These steps create a basic collection. Check out Create a Remote Desktop Services collection for desktops and apps to run for more information about collections.
- In Server Manager, click Remote Desktop Services > Collections > Tasks > Create Session Collection.
- Enter a collection Name (for example, ContosoDesktop).
- Select an RD Session Host Server (Contoso-Sh1), accept the default user groups (ContosoDomain Users), and enter the Universal Naming Convention (UNC) Path to the user profile disks created above (Contoso-Cb1UserDisks).
- Set a Maximum size, and then click Create.
What Replaced Remote Desktop Manager
You've now created a basic Remote Desktop Services infrastructure. If you need to create a highly-available deployment, you can add a connection broker cluster or a second RD Session Host server.
